By: Tom Hilton | Posted: November 9, 2020 | Updated: April 5, 2023
If you understand your vulnerabilities, you will be alert to situations that put you or an aging parent at risk.
If you understand how common scams work, you are better prepared to guard against them
While technology exists that can reduce our vulnerability to scams and hustles, technology isn’t fool-proof. Thus, it would be a mistake to reassure ourselves that giving mom a new cellphone designed for the elderly, or installing new anti-spoof software to protect your wife from bank fraud will prevent them from being scammed. It usually helps, but there is no guarantee. You still have to be vigilant.
It is worth keeping in mind that the best protection against exploitation by scammers comes from having a general understanding of how people try to con the elderly into sending/wiring them money — or worse, giving them the electronic keys to their financial kingdom.
If you understand your vulnerabilities, you will be alert to situations that put you or an aging parent at risk.
Nearly all scams try to steal the target’s identity one way or another. Below are the most popular ways scammers try to do that.
This article is part of a longer series entitled “Scams & Older Adults: What to Do?”
Types of Scams
1. Phishing.
a. Spoofing and “Fishing Lures”
Scam emailers, postal mailers/fliers, and phone callers can spoof their identity with fake email or postal addresses, logos, and phone numbers – even numbers displayed on your smartphone.
Spoofs work just like lures used to attract fish – only you are the fish and scammers want to reel in your identity, your personal information. Once they get the information they are fishing for, they will likely toss you back into the water oblivious to the fact that you are about to be robbed.
Spoofing is not that tricky – just illegal – and it is rarely prosecuted.
Scammers make their fishing lures look or sound like your bank, service provider, merchant, or credit card company. Their bait is usually offering too-good-to-be-true deals on credit card interest rates, insurance policies, warranty extensions, etc. However, some scammers use fake alert calls or emails to panic their victims into providing personal information without thinking. Fake alerts claim that there’s been some “suspicious account activity” like fraudulent purchases or they discovered an error in your account information.
Callers usually ask you to provide personal information over the phone. However, this scam presents a high risk that you will start to get suspicious and hang up. To avoid that, many scammers use the approach favored by email scammers. They provide a hyperlink to click on using a text message. Internet links, whether texted via phone or provided via email or postal mail, take you to their scamsite – often a spoofsite.
b. Scamsites and Spoofsites
A scamsite looks and works just like any legitimate bank, merchant, or insurance company site.
The purpose of a scamsite is to get you to fill out application forms with enough personal information to steal your identity. In contrast, the purpose of a spoofsite is to steal your login credentials.
A spoofsite is a form of scamsite that tries to look just like your current bank, credit card, or insurance company login page.
Once you log in, it might actually open your real account website using the credentials you entered simply by linking to the real site and echoing what you typed. This can also be accomplished by use of “bots” which is malware often attached to things you download, like photos.
One way that might help to identify a spoofsite is by close examination of the web Uniform Resource Locator (URL) address.
It might at first blush look like your real bank’s address; for example: www.MyBank.org. However, upon close examination you might notice a subtle difference you failed to — for example, that the bank web address showing in your browser is actually www.MyBank.net and not www.MyBank.org (your real bank). Some spoofers do not even hide the IP address and you might see something lile a string of numbers and letters.
It is a snap to create a copy of a website and make it look and act like the real deal. No matter how legitimate a letter/flier or email looks, or a call sounds, ignore it/hang up, and call your service provider, merchant, or bank’s customer service number directly.
Of course, the best way to avoid being fished is NEVER CLICK WEBLINKS ON TEXTS AND EMAILS. Always use the address you always use from your browser bookmarks or wherever you record web addresses, logins, and passwords.
Hacks (Malware & Viruses).
Hacks are direct attacks on your operating system that enable outright information theft as well as theft of your entire device.
You can only be hacked if you download malware or other viruses. Malware and viruses are like fishing, except once you unintentionally bite the bait, hackers steal your Internet bandwidth, your files, or make your entire PC, tablet, or phone inoperable until you pay a ransom.
You are lured to unintentionally install malware when you download an innocent-looking file, play a video, or click a link to a scamsite or spoofsite.
Here are two common ways your PC, tablet, or phone might get hacked:
- Unsecured public WI-FI networks; and
- Infected downloaded files.
Wi-Fi-Faux-Fumbles.
Public Wi-Fi networks (especially airport, hotel, and restaurant Internet access) are notorious for malware hacks because anybody can access them like the telephone party-lines of the 1950’s.
Public Wi-Fi can enable an attacker to login and take control of the router then load malicious scripts, or even change the DNS server so that all traffic is directed to an IP owned by the attacker.
Many hackers just want to monitor your Internet activity to detect and steal login credentials to your bank, office, retail accounts, etc. An even worse hack outcome is making you a superspreader by stealing and using your contacts information to circulate more malware and viruses by spoofing you to your friends. Because you are friends, they open the email they think you sent, download the file (like a picture or video) containing malware and now your friends also have the virus.
Always activate your VPN (virtual private network) service before logging onto a free Wi-Fi service. Most anti-virus services offer VPN access.
Infected Downloads.
A common scam is when you receive a photo or video of something cool or cute that the sender claims to have downloaded to share with you.
Facebook, Instagram, and Twitter are notorious tools hackers use to spread malware via the site’s messaging facility. Porno pics make excellent hacker bait as well.
Downloading naughty pictures or videos without a good antivirus service installed makes being hacked inevitable. Once in a while, I get Facebook messages from friends who rarely interact with me that have a video, web address, or picture attached.
The scam message is often tersely worded like: “Thought you’d get a kick out of this.” Or “Here’s a good one.”
I always stop and ask myself why didn’t they just post this publicly or email it? Usually I hit the delete key to be safe.
Here are three common types of malware hacks you might unwittingly enable:
- Trojan Horses. When you download some innocent pics and vids, they unleash malware or spyware that might track every future keystroke or find and copy personal information to access your financial accounts and services.
- Hijacks. When downloaded, this type of malware lets people steal some of your Internet bandwidth or hard drive storage to create a virtual server composed of linked home computers. You pay for 100MPS service, but the hacker highjacks 80MPS of it for free – often to use for illicit purposes. It is like stealing $50/month from you. To add insult to injury, you have slow service.
- Ransomware. Worst-case scenario is that your phone or PC is kidnapped. You turn them on and the screen says call this number to unlock your PC (or phone). While you hear about this happening to hospitals and cities – it happens to home users too. This malware can be nuclear in that failure to pay will wipe your files and even turn your PC into useless junk. Paying is no guarantee that your identity will not be stolen as well.
Skimmer & Shimmer Scammers.
Aside from conning you or a parent into volunteering your credit or debit card account number and Card Verification Code or PIN, scammers can also steal your account access right off your card using skimmers and shimmers. When you swipe your card on a hacked gas station pump, ATM, etc. the skimmer or shimmer steals all its encoded information to create a duplicate later.
Skimmers
 Skimmers are devices that read your magnetic strip when you enter your credit card into the slot. They are often easy to spot because they do not match the rest of the machine or if you jiggle them, they wiggle.
Skimmers are devices that read your magnetic strip when you enter your credit card into the slot. They are often easy to spot because they do not match the rest of the machine or if you jiggle them, they wiggle.
They are typically installed on machines with low surveillance. Thus, it is best to use ATMs inside stores, hotels, and banks – not on the street.
Skimmer-scammers are often unable to get your information if you wiggle your card as you insert it. It makes it hard for the skimmer to read the magnetic strip. ATMs use a chip reader after they swallow your card, so wiggling it should not reject your card.
I am not aware of a good way to tell you have had your card “skimmed”, thus you are unaware that somebody can empty your checking account at will.
ATM skimmers usually want your PIN code too, so they put a tiny little spy camera nearby to watch you log in. Cameras can be foiled by covering the keys with one hand while punching in the number. Can’t spot the camera? Were you looking for a small drill hole? Did you notice the extra little LE strip lite over the keys? Did you look into the overhead light? It was right there, but the light blinded you.
Waitergators
 Waitergators are human skimmers.
Waitergators are human skimmers.
You have lunch and hand the waiter your credit card to pay the bill. He disappears and returns with a receipt to sign and you go merrily on your way.
However, s/he was a waitergator who noticed that your card was from a foreign bank and snapped it up like a lurking alligator. They first swipe your card into the restaurant reader, then again on an attachment to their smartphone for instant transmission to an accomplice.
Waitergators are very hard to catch when they predate foreigners, because travelers use credit cards for most meals. Thus, after a day or two it is impossible to determine which restaurant in which city stole your card.
Shimmers
Shimmers are nasty devices that read your card chip inside the machine.
They are less common, and again, require tampering activity easily spotted by surveillance cameras – or service staff in stores. There have been cases where employees colluded with shimmer scammers to install the devices – even in grocery store checkouts. If your ATM has one installed, you are unlikely to detect it. But if you cover the keypad as you enter your PIN, you might improve your odds of not being shimmer-scammed.
Examples of Scams
In 2019, there were 3.2 million scams reported to the federal government. The actual number of scams is likely way higher because people are embarrassed to admit that they were fooled.
Scammers have 2 main goals: either outright theft of money or identity theft.
- Outright theft scammers try to get you to send them money via Pay-Pal, bank wire, or credit/debit card.
- Identity theft is far worse because if they can get you to volunteer your personal information (Full name, address, phone number, bank account number, social security number, driving license number, credit card number, employer, job, years with the company, etc.), they can open accounts in your name. If they can steal your login credentials for your bank using a spoofsite, they can move money from your account into theirs.
FBI Common Elder Fraud Schemes
- Romance scam: Criminals pose as interested romantic partners on social media or dating websites to capitalize on their elderly victims’ desire to find companions.
- Tech support scam: Criminals pose as technology support representatives and offer to fix non-existent computer issues. The scammers gain remote access to victims’ devices and sensitive information.
- Grandparent scam: Criminals pose as a relative — usually a child or grandchild — claiming to be in immediate financial need.
- Government impersonation scam: Criminals pose as government employees and threaten to arrest or prosecute victims unless they agree to provide funds or other payments.
- Sweepstakes/charity/lottery scam: Criminals claim to work for legitimate charitable organizations to gain victims’ trust. Or they claim their targets have won a foreign lottery or sweepstake, which they can collect for a “fee.”
- Home repair scam: Criminals appear in person and charge homeowners in advance for home improvement services that they never provide.
- TV/radio scam: Criminals target potential victims using illegitimate advertisements about legitimate services, such as reverse mortgages or credit repair.
- Family/caregiver scam: Relatives or acquaintances of the elderly victims take advantage of them or otherwise get their money.
- Investment scam: An email or call says they can increase your return on investment by letting the scammer manage your investments, or invest in their new technology company and double your money in 6 months.
Here Are Some More Example Scams:
1. Be Wary of Callers Announcing an Emergency or Problem.
Elderly callers are easily shaken up when called about an accident, arrest, hospital admission, assertions that your account has been compromised, etc. Here are four common examples:
a. Bail Out Your Grandson Calls
“Hello Grandma, this is Billy (your grandson’s name who lives in a different state). I’m in a terrible jam. I was at this bar and a fight happened and they arrested all of us. I need $500 wired to a bail bondsman to get out of jail. Please help me. I don’t want mom to know I am in jail for underage drinking. The cop said he would drop the charges when I appear in court, but I cannot get out of jail without bail money.”
The fake Billy will give you a PayPal account or bank account to send or wire the money to – and you are out $500. They almost got away with this scam on my late mom.
b. Bogus Charge Warning Calls
“This is VISA Card. We are calling to inform you that a charge of $399.72 will be made against your card to renew membership in Palm Beach Yacht Club. If you wish to continue your membership this is just a courtesy call. If you think this charge is in error, please press 1 now to speak to a representative… “
HINT: That is when you hang up.
I get 4 or 5 calls like this every year. The charge is clearly one you never made. That is how the scammer baits the hook to get you to press 1 so the fake representative can pump your for personal information needed to steal your identity. Note they often use odd dollar amounts to make it sound real?
c. Recent Security Breach Calls
“Hi Mrs. Doe. This is Melissa Brown calling from VISA Card. We believe that there has been a security breach and your credit card number might have been stolen. If you can give me your current VISA number, I will check it against our list of stolen numbers.”
- “Sure dear, it’s 4444 5555 5555 6666.”
- “Glad I asked. It is on the list. Never fear. You are insured for any bogus charges. Before we can issue a new card, I need to verify that it is you. What is the three-digit number on the back of your card? “
- “It’s 456.”
- “Great. It’s really you” – ha-ha. “Please give me the address you would like me to overnight FEDEX a replacement VISA card.
- “123 Adams, Sucker, WA, 32321.”
- “And what name do you want on the new card?”
- “James E. and Martha P. Doe.”
- “Great. I will get right on that.””
Not only did you give out your VISA card number to a stranger, you provided the name on the card, the Card Verification Code, and the home address. PS: Don’t hold your breath waiting for the new card.
HINT: As a rule, never give out credit card numbers and Card Verification Codes if somebody called YOU. When you make phone purchases you know who you are calling because you dialed the number.
If you get such a call, tell them you will call right back, then look up the emergency number on the back of your card or in your smartphone contacts file and call them. That way you are using your card number to identify you to a verified service representative – not a scammer.
d. Utility Company: Voicemail Scam
“This is the electric/water/sewer, etc. company. This is your final notice that we will be turning off your service within 24 hours for non-payment for services. If you think this notice is in error, please call 888-888-8888 or press star now.”
If you press *, the caller who answers will either (A) pump you for personal information and steal your identity, or (B) demand a temporary security deposit charged to your credit card to ensure service until the matter is fully investigated.
HINT: Utilities never shut off service without gobs of written notice – by law. If you are really that far in arears, they will want cash. Hang up, call the utility company using the number on your monthly statement, and explain what happened. 99% of the time, it is a scam.
2. Be Wary of Callers Claiming to be Your Bank or the Police.
Elderly callers are often more trusting of police, bank, and utility company personnel. Here are two examples:
a. Donation to the Police or Firefighter Calls
“Hello, this is Trooper Sam Smith of the Highway Patrol calling as part of our annual Save The Teens program to reform juvenile delinquents.”
“Can we count on you for a $100 donation this year? Great! All I need is your credit card number and 3-digit verification number on the back. Do you still live at 101 Hobbs Drive in Weymouth MA? Great. And is your phone number still 345-333-4563? Super. Okay, what is that card number again? 3333 4444 4444 3333. Thanks!”
You just volunteered your credit card to somebody pretending to be a cop.
HINT: Trooper Sam just asked to verify the number he called YOU at? I have an out-of-state phone number. The real cops would know I moved 8 years go out of state. It was a robo-call scammer. I get several of these annually.
b. Updating our Records Calls
“Hi, this Berenice at XYZ bank. We’re calling to update our records. Can you spare a minute?”
“Great. I’m seeing that you are John P. Doe born Dec 2nd 1967. Is that correct? Great Mr. Doe. Now I am showing your wife as Sharon Doe? Yes. Great. And your checking account is 4434 8277-433, right? No, it is 5634 8544-978. Oh, let me correct that for you right now – so sorry for the error.
You just gave a stranger your checking account number because she already looked up you and your wife’s full name and birthday on the Internet.
HINT: If you get a call from your bank, asking YOU for information they should already have, assume it is a scam and hang up.
Just to be sure, call your bank at the number you normally use, and ask if they just called you to update their records. The answer 99/100 times will be no. If the answer is yes, then log into your bank account and update your profile information. Never use an embedded email or phone text message link which could take you to a site in India or Ukraine – who knows?
3. Some Scams Come in your Email or Postal Mail.
Not all scams come from smartphones or emails. Some start with postal mail. They basically employ the same scams described for the Internet and email so there is no need to repeat them. There is usually an easy way to spot a spoofed email which I describe below.
a. Investment Fraud.
Never do business with an investment company that calls YOU unless it is your own broker.
Successful companies do not recruit customers via phone or email. Ever get a call from Raymond James or Charles Schwab asking you to switch to them? Scammers invite you to dinner at a swank restaurant to pitch their scams. Great meal, too many free drinks, now let me tell you how to double your money with our new Timeshare Package, or Asian-Pacific Hedge Fund, etc.
You wind up paying premium prices and you will be lucky to break even in a year due to high service charges or just outright theft.
b. Installing a New Record System: Email Scam
You receive an email from Hometown Water and Waste Company with their logo on the email. They are announcing a new billing system to streamline on-line billing and the ability to offer auto-payments – no more check writing.
“Click the link at the bottom of this email, and fill in the form that appears. We will confirm your enrollment in a separate email tomorrow.”
Like a sap, you click the link and a form with the same logo as your last bill appears. You dutifully complete the form providing your checking account and credit card number along with a personal number to call. Now the sender, using a spoof email address and his spoof website can drain your checking account and buy a mink coat with your credit card.
HINT: Even if this was a legitimate request, again, never trust a link on an email – always go to your online account via bookmark or IP address, and log in like always.
How to Detect a Spoofed Email.
When I get unexpected emails from service providers or utilities, the first thing I do is click on the down arrow after my name in the address. It might look something like this:

But when I click the little down arrow symbol after “To: Me” this is what I might see:
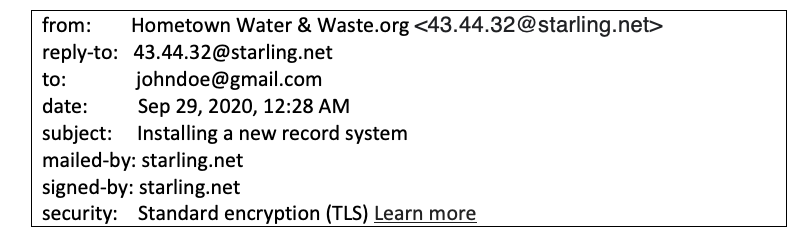
The actual email address is some numbered account at starling.net whatever ISP that is.
It should have read “Hometown Water & Waste.org < HW&W@Hometown.org>” or something ending with @Hometown.org as that was in the email header. So, when you click that little arrow to get the full routing information on the email, and what appears is not the same – get very suspicious!
Now it is possible that the hometown water service hired a new company to manage its accounts. Nevertheless, it is wise to call to confirm. My own gas company, Florida City Gas Company, just did exactly that last May. They switched account management firms. They did include a warning letter with the bill. They foolishly did not migrate old account numbers and required all customers to get new account numbers – suspicious from the start – even though legitimate!
This was the most incompetent switchover I ever experienced because there were so many possible scams in their irregular procedures. You need utilities and they are a monopoly, so you have to tolerate their incompetence, but you can be extra cautious.
More: The “Scams & Older Adults” Series
This is part 2 of the “Scams & Older Adults” series. See the entire series below.
1. Start here: Read “Scams & Older Adults: What to Do?”
2. Forewarning involves learning how scammers and crooks try to rob you. Read “How Scams Work“.
3. Forearming includes a variety of actions you can take to reduce your or your loved-one’s vulnerability to being scammed. Read “How to Avoid Scams and Defend Against Them“.
4. When to Step In and Take Control discusses situations when you need to be more proactive. Read “Elderly Scams: When You Need to Take Control“.
*Disclosure: The research and opinions in this article are those of the author, and may or may not reflect the official views of Tech-enhanced Life.
If you use the links on this website when you buy products we write about, we may earn commissions from qualifying purchases as an Amazon Associate or other affiliate program participant. This does not affect the price you pay. We use the (modest) income to help fund our research.
In some cases, when we evaluate products and services, we ask the vendor to loan us the products we review (so we don’t need to buy them). Beyond the above, Tech-enhanced Life has no financial interest in any products or services discussed here, and this article is not sponsored by the vendor or any third party. See How we Fund our Work.

